High-compute unstructured extraction.
Owlyscan reduces intelligence production cycles from months of manual reading to hours of automated computation. Our Large Language Models (LLMs) are specifically engineered to read, translate, and contextualize chaotic data formats found within unindexed threat vectors.
01 // Dynamic Ecosystem Mapping
You do not need to upload static lists of thousands of vendors. Simply provide a broad search parameter—such as the name of a specific defense program, a joint venture, or a corporate entity. The system autonomously discovers and maps the undocumented supply chain network connected to it.
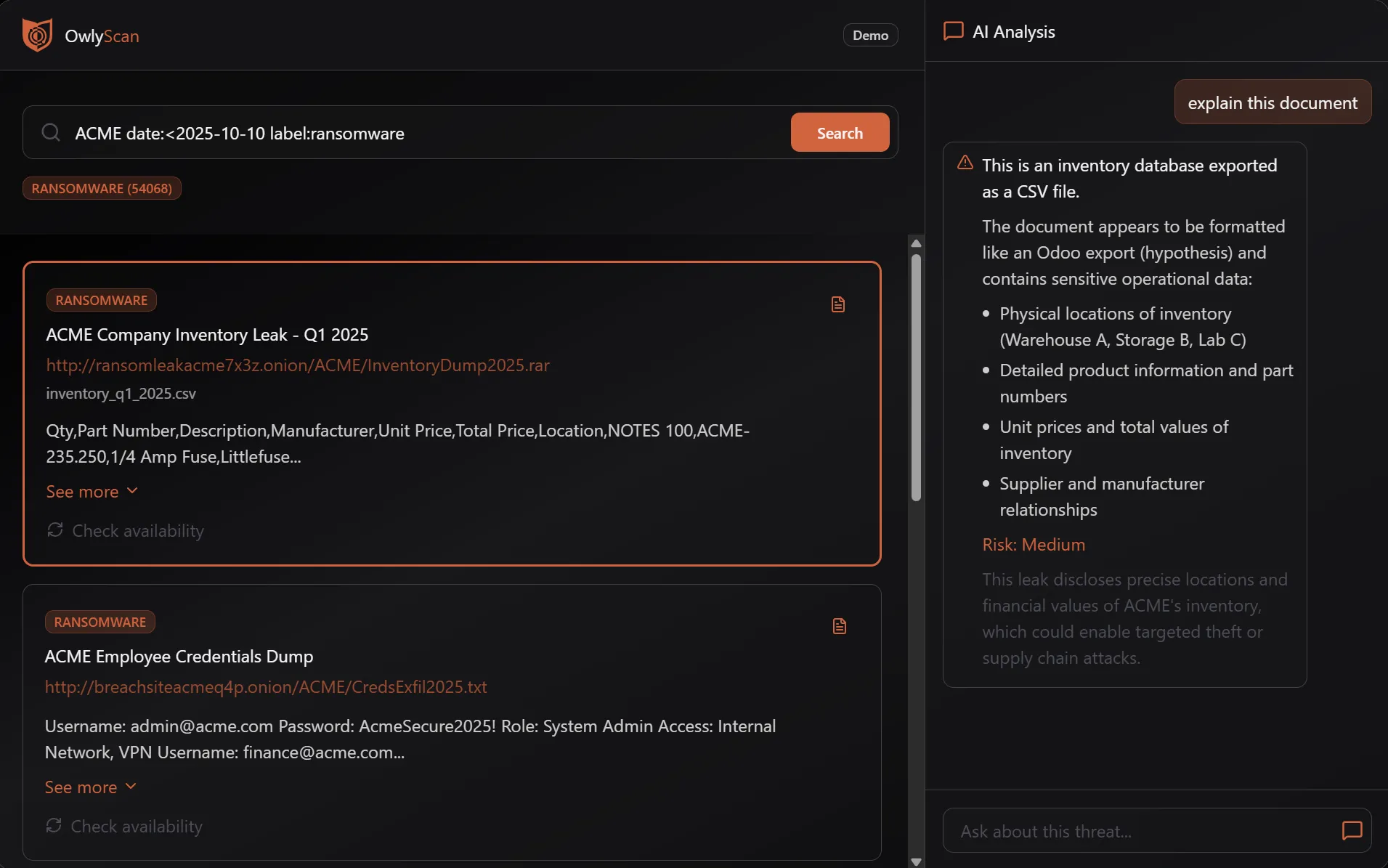
USER QUERY
Find everything about the ACME project
SUMMARY • ACME PROJECT
Key Findings
Reasoning
Cross-referenced leaks indicate Acme Corp involvement in ACME via fictional framework, linking to corporate development initiatives with AI integration and tech dependencies.
Leaked Doc Excerpt
...Structure of views and project approach for fictional framework from Acme Corp perspective...
Summary of Discovery
Discovered ACME-related docs in leaks, detailing project structures and Acme Corp strategies.
02 // Deep Content Indexation
The engine extracts and analyzes content from virtually any data format, whether proprietary or open. From complex nested archives and standard PDFs to specialized industry files, we bypass the limits of basic keyword searches to comprehend the actual text inside the documents.
Ecosystem: Ransomware
1 / 160Import from
example.onion/archive/acme.tgz
example.onion/archive/acme.tgz/Confidential_Design_Framework.docx
Confidential_Design_Framework.docx
...Figure: Structure of views and project approach for fictional framework. Involves major tech firms; focuses on future systems integration...
2025-09-26
03 // The Evidentiary Ledger
AI-generated summaries are a liability without proof. Every claim in our strategic briefing is directly linked to the exact source file. We provide the original document name, the precise page number, and the surrounding context. This guarantees 100% verifiable intelligence with zero AI hallucinations.
Strategic Capabilities.
Owlyscan executes episodic audits and persistent over-watch for highly regulated sectors. Due to the high-compute nature of our infrastructure, we focus exclusively on macro-ecosystems and do not audit single IT perimeters.
M&A Cyber Due Diligence
Standard cyber audits check a target company's active IT defenses. Owlyscan goes deeper by investigating the target's historical supply chain. If intellectual property has been exposed, deal teams receive precise evidentiary proof to adjust valuations. If the ecosystem is clean, we deliver a Verified Clearance Report, giving your Investment Committee total confidence before signing a term sheet.
Sovereign Ecosystem Over-Watch
Engineered for air-gapped, on-premise deployment. Owlyscan provides Sovereign Commands with an autonomous extraction engine that maps international supply chains and indexes unstructured threat exposures, maintaining absolute national data sovereignty and uncompromised OPSEC.
Post-Breach Legal Forensics
Following a corporate data exposure, legal counsel faces strict regulatory notification windows. Owlyscan rapidly processes high-volume public exposures to isolate regulatory liabilities, identifying exposed executive communications and PII with exact page-number citations, allowing legal teams to seize control of the narrative.
Intelligence Subcontracting
Analyzing entire economic sectors requires processing terabytes of data. Owlyscan serves as a high-compute backend for economic intelligence consultancies. We automate the ingestion of public threat data to generate comprehensive evidentiary ledgers, which you can white-label as technical annexes for your own clients.
Competitive Ecosystem Mapping
Using strictly Open Source Intelligence (OSINT) methodologies, Owlyscan maps the supply chain structures of competing industrial programs. By analyzing public threat environments, we identify shared subcontractors and exposed operational data to provide verified strategic context to corporate planning units.
Sectoral Threat Baselines
Public-private cybersecurity hubs and national competence centers require empirical data to validate policy initiatives. Owlyscan conducts comprehensive, sector-specific threat censuses to provide anonymized, aggregated reporting on the exact volume of compromised intellectual property across a region or industry.
Engineered for Sovereignty.
A high-compute intelligence engine delivered as secure Sovereign SaaS by default, with air-gapped architectures available for classified defense networks.
Sovereign SaaS Cloud
For Primes, Consultancies & Critical Infrastructure
- Single-tenant SecNumCloud-certified environment
- Managed GPU compute on European sovereign soil
- Full data sovereignty over targets and outputs
- Our primary delivery model
Commissioned Audits
For M&A Due Diligence & Crisis Law
- Zero IT integration required
- One-time macro-ecosystem audit on sovereign infrastructure
- Evidentiary Ledger delivered to your legal or deal team
- Secure end-to-end chain of custody
Air-Gapped (On-Premise)
For Defense & Intelligence Agencies
- Absolute network isolation guaranteed
- Owlyscan LLM deployed on your disconnected GPU supercomputers
- Strategic directives never touch external networks
- For organizations requiring full air-gap compliance
Deployment models tailored to your classification level.
Our Clients
OwlyScan is developed by SitinCloud, a proud member of GICAT, the French industry group for defense, land, and aerial security. This affiliation reflects our commitment to providing cutting-edge tools tailored to the unique needs of professionals in high-stakes sectors.
Our clients include:
- Red teams
- Remediation Companies
- State services
- Industrial Companies
Send us a message
Have questions or need assistance? Our team will get back to you within 24 hours—guaranteed.
Give us a call
+33 5 64 27 05 82
Visit us
2 avenue du Président Pierre Angot, 64000 PAU